🍪#1 The Dangers of Insecure File Uploads
From RCE to data leaks—the risks behind insecure file handling.
Hi Everyone,
Welcome to the 1st drop of the Secure Cookie newsletter.
As you know, file uploads are a common feature in modern web applications—profile pictures, documents, reports, media sharing, and many others. But behind their convenience lies one of the most dangerous vulnerabilities: insecure file upload.
When applications don’t properly validate the files users submit—their name, extension, content, or resource usage—attackers can exploit this to upload malicious files. From there, the consequences can quickly escalate.
Why Insecure File Uploads Are So Risky
A poorly protected upload function can serve as a gateway to severe attacks:
Remote Code Execution (RCE): Malicious scripts uploaded and executed on the server can give attackers full control.
Cross-Site Scripting (XSS): Uploaded HTML, SVG, or other files containing scripts can be used to hijack user sessions, steal data, or redirect to malicious sites.
SQL Injection: File names used directly in database queries without sanitization can drop tables or exfiltrate data.
Command Injection: File names passed to system commands can execute arbitrary code.
Parser Flaws: Vulnerabilities in file parsers (PDF, XML, media) can be abused for crashes or code execution.
Path Traversal: Manipulated filenames (../) can traverse directories, exposing or altering sensitive files, enabling defacement and integrity loss.
Data Leakage: Metadata or hidden content inside files can expose sensitive information.
Malware Delivery: Files can carry different types of malware targeting servers or end users.
Phishing: Disguised uploads (e.g., invoices, HR docs) can trick employees into revealing sensitive information.
Denial of Service (DoS): Oversized or excessive uploads can overwhelm server resources, disrupt network performance, or limit storage capacity, causing service downtime.
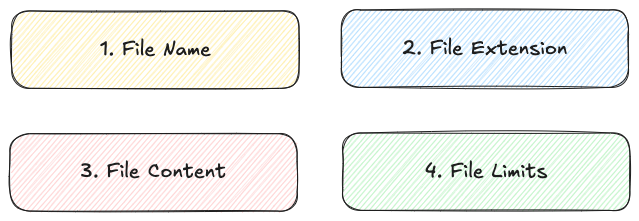
Components Attackers Exploit in File Uploads
When it comes to insecure uploads, attackers don’t just rely on a single trick—every part of a file can become an attack vector if left unchecked.
File Name
Manipulated names can include path traversal sequences (../) to escape directories, overwrite sensitive files, inject malicious SQL payloads to alter queries and exfiltrate data, or even trigger commands when passed to system utilities.
File Extension
Executable files (.exe, .elf) can run malware or perform unwanted actions, while source files (.php, .js, .py) may be interpreted by the server, leading to arbitrary code execution. Even compressed files (.zip, .tar) can smuggle multiple malicious payloads.
File Content
PDFs, office docs, and media files can hide embedded scripts, obfuscated payloads, or parser exploits. Some uploads are crafted for phishing—appearing as invoices or reports to lure victims into revealing data.
File Limits
Oversized or repeated uploads can consume CPU, RAM, bandwidth, or storage, leading to resource exhaustion and potential Denial of Service (DoS).
How to Secure File Uploads
Because there’s no single silver bullet, securing file uploads requires a defense-in-depth strategy—multiple layers of validation, sanitization, and controls. The goal is simple: no file should ever be processed or stored unless it has passed every security check.
Key Best Practices
Start with general validation: Ensure that any existing general input validation process is performed prior to other validation steps.
Sanitize file names: Generate random names (e.g., UUIDs) for storing or enforce strict allow-lists for characters and length.
Control extensions: Only allow business-required extensions; block absent and redundant extensions.
Check actual content: Verify file type against its data and scan with antivirus or sandbox tools.
Set limits: Enforce maximum file size and prevent excessive or repeated uploads.
Harden storage: Store files on a dedicated service or at least outside the webroot, enforce least-privilege permissions, and avoid execute rights.
Require authentication: Restrict who can upload and who can access uploaded files.
Use trusted frameworks: Leverage mature libraries for preprocessing instead of reinventing validation.
Protect against CSRF: Ensure upload endpoints are safeguarded against Cross-Site Request Forgery (CSRF).
Stay updated: Keep dependencies and parsing libraries patched and securely configured.
In the upcoming posts, I’ll break down each of these practices in detail, showing how attackers exploit weak points and how to implement the right defenses.
Reading Picks
Here are a few articles I found valuable in recent weeks: